Overview
Nullstring's Prison Clear Payphone Back Pack is the best of ideas come up with in response to the question “what is the dopest thing you could make Prison Clear?”
Do you remember the Conair landline phones from the 80s and 90s? The clear ones, with all the colors inside? Envision that, but its a payphone! Now, double down on that because its a fully wireless, battery-powered, properly functioning payphone on a back pack frame!
I Want One!
You can't have one! BUT! You CAN have a BananaPhone! A BananaPhone is the core and heart of the Payphone Back Pack! It is a USB-C adapter to connect landline phones to your cellphone!
COTS Iterations – Gross, Bluetooth!
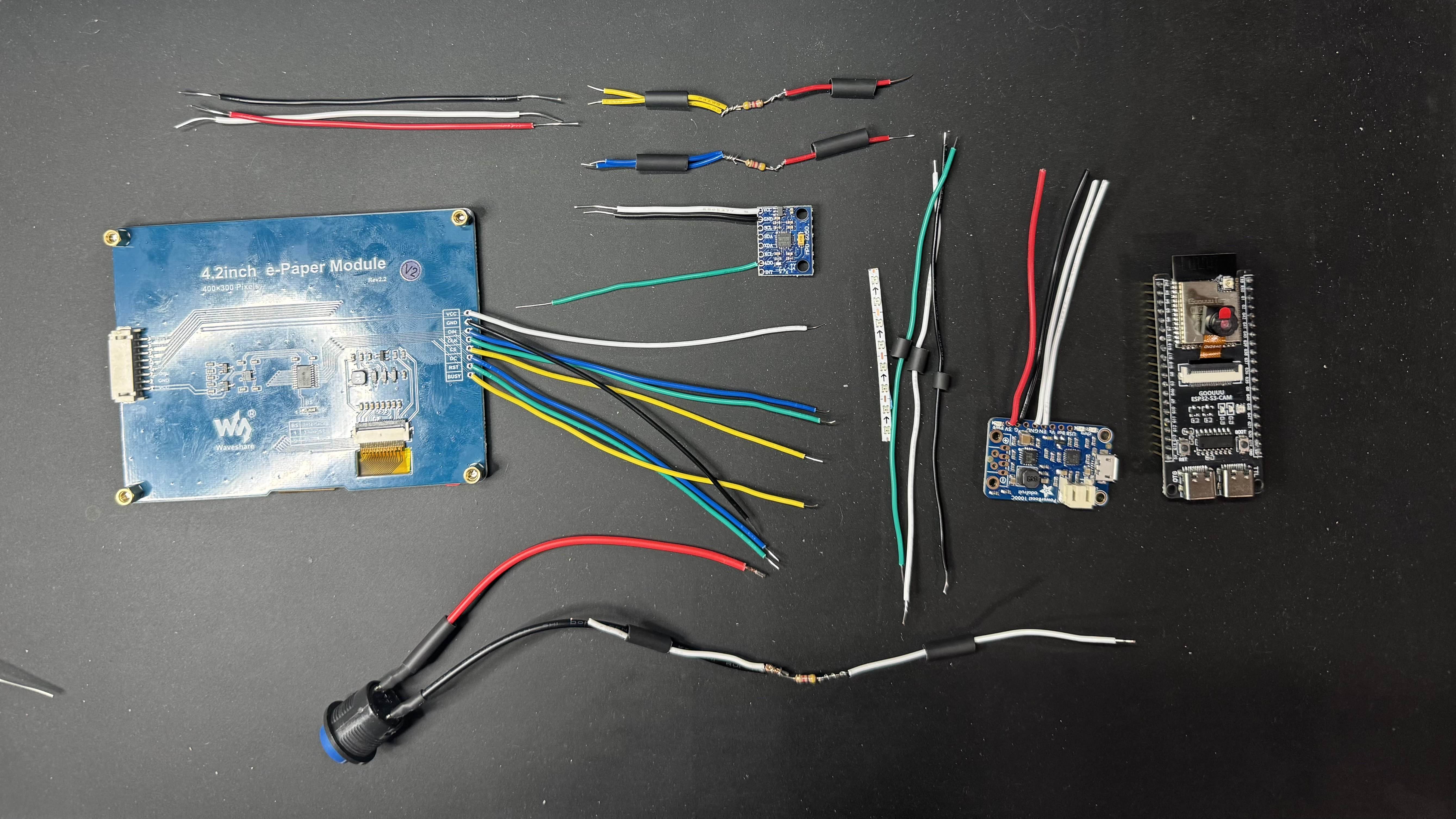
todo: describe the cell2jack and xb2, describe the COTS demo taken to DEF CON, describe how these COTS devices are marketed to olds who still want to use a landline phone, all of them lack wired connections, and its not cool to solve it this way – so, we design our own usb audio class device instead. add a photo or two of the COTS demo.
- Cell2Jack or XB2
- Cellphone
- Landline Phone
- LIPO Pack
Not good enough!
Original Payphone Parts Used
- Western Keypad/Hook assembly
- MEI Coin Mechanism
- Hotwired Elcotel Mainboard
Housing Design
todo: describe the process of measuring the real housing and creating CAD models, making changes to accommodate modularity and cheaper fixes if there are issues down the line and also to accommodate SLA printing process.
Can we cast it?! No!
todo: describe the issues with trying to make a casting mold from something like a weather proof painted payphone housing thats all rusty and old and also very large and covered in bits and bobs.
3D Modeling
todo: discuss the process of measuring and modeling the payphone housing
first in tinkercad “how hard could it be”
todo: add some screenshots and discuss how shitty tinkercad becomes the more complex a model becomes, and how it fails to export high enough quality meshes to be able to be large scale sla printed successfully
then in fusion “how much harder can it get”
todo: add some screenshots and discuss some of the differences between my housing and the normal housing, some of the changes made to support sla printing, and some of the changes made to support modular assembly so if something doesnt mount right the entire model does not need to be re-printed at incredible cost
Printing
FDM Test Printing
todo: add photos here
Large-Scale SLA Printing
Yet to do this because tariffs make it insanely expensive and I would like to only do it once.
BOM Generalized
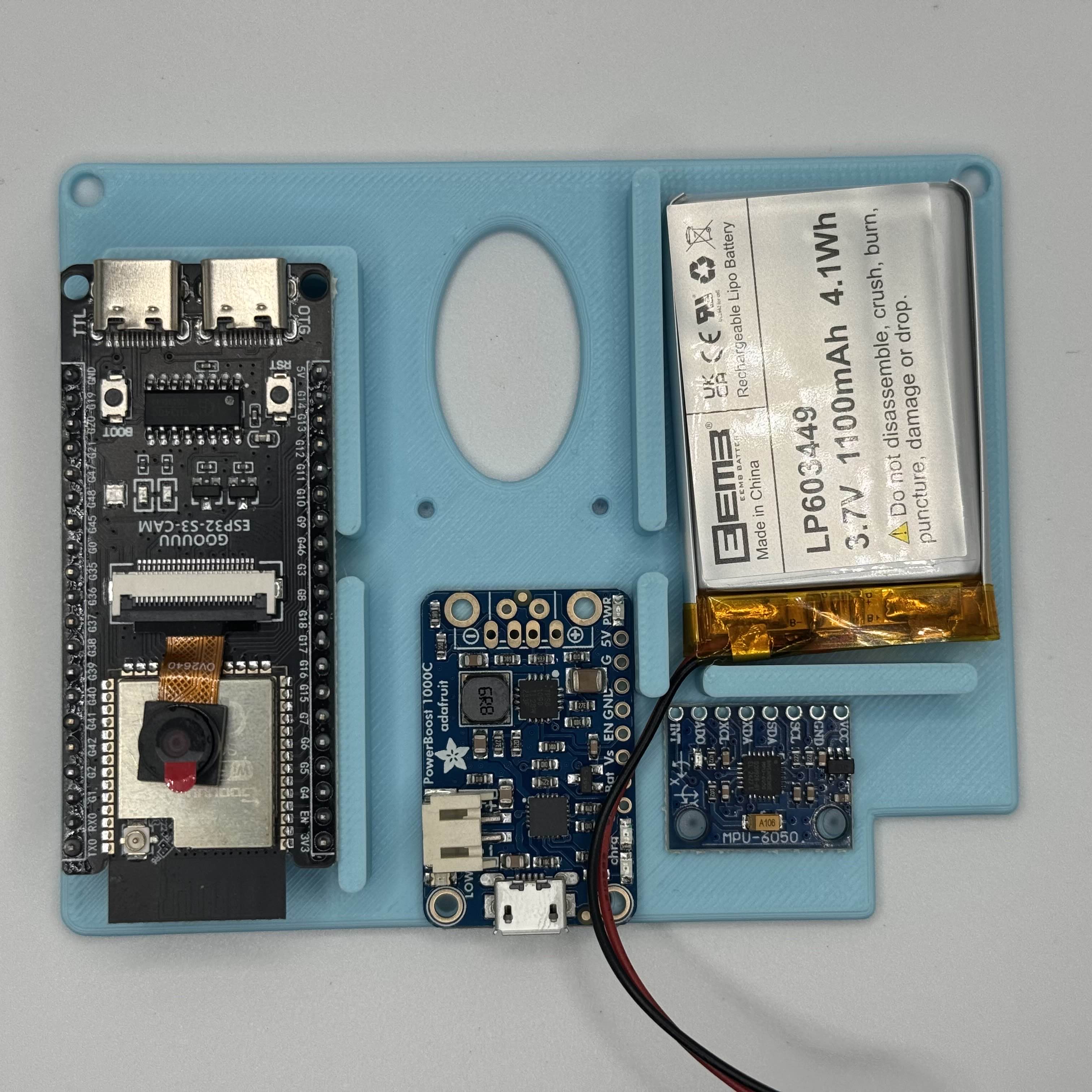
Controller Board
- Custom SAMD51 board
- Fully isolated high-speed USB 2.0 Audio Device Class – “USB Headset”
- ProSLIC-based FXS with Quasi-Cuk HV circuit and built-in DAC
- SD storage
- 32x32 RGB LED Display (front interior of coin box)
- 5” 3-Color E-Paper Display (center front branding card)
- 1.5” Transparent OLED Display (front top left volume button / sticker)
- 1” OLED Display (number card)
- GPIO for operating relays for EL-Wire and Discrete LEDs
- GPIO for operating Coin Mechanism
- Many WS2812 RGB LEDs
- LiDAR Detection (to know when its photo is being taken)
- LoRA Meshtastic Sidecar board
Power Board
- Fused input from 12v 50aH LiFePO4 battery with onboard BMS
- 4x Fused Output Rails: 3.3v@4a, 5v@4a, 5v@5a, 12v@20a
- MOSFET-based Remote GPIO+Physical Switch Controls Per Rail and Main Cutoff
- INA219 for Voltage Monitoring
- Multiple discrete EL-Wire inverter boards
- Rail-direct, GPIO controlled relays for LEDs and other components
Features
- Wireless, battery powered, back pack mounted functioning payphone – But Clear and Colorful!
- Any amount of change lets you place a call!
- Incoming and outgoing calls completed via cellular network
- Full Redbox support
- Bluebox minigames facilitated by an onboard simulated POTS network
- It blushes when you take its photo with an iPhone Pro
- It has FOUR displays! and EL-WIRE! and LEDs!
- It might read received text messages aloud!
When Can I See It?!
Project State
ConceptBuy a payphone, strip and gut ittry to use housing to make casting mold – this failsbegin using housing for measurements for CAD modelwork in tinkercad – it becomes a nightmarework in fusion, far far far better, learn a lot that ends up propelling other projectsacquire or make Western/GE style handset – BUT CLEARstart FDM prototyping the housing modelwaste a bunch of money on wrap and paint and heatshrink for when its time to make it colorfultry prototyping with samd21 and KS0835 SLICs – find this to be saddled with too many problems and no way to solve themdesign samd51-based board which can handle everything including the DAC stuff internally and well- Breadboard Final COTS assembly and tests
- Boards Final Design, Order, and Testing
- Housing Model Final Adjustments and Order
- Final Assembly and Testing
- Take it on Tour
Upcoming Appearances